WHAT IS RANSOMWARE?
First, let me aware you about the Ransomware what is ransomware?
Ransomware is a type of malware that aims your basic information data and machine for the motivation behind blackmail or you can say extortion. Ransomware spreading all over the world via fake emails or spearphishing emails. After attacking your PC’s via Ransomware the cyber actor demands a ransom payment request as a recovery installment. After accepting installment, the cyber actor will purportedly give a road to the casualty to recover access to the data or system. Recent iterations target enterprise end users, making awareness and training a critical preventive measure.
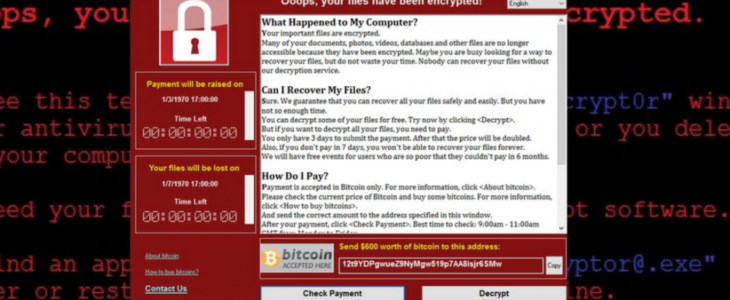
The ransomware, otherwise called “WanaCrypt0r“, “WeCry“, “WanaCrypt” or “WeCrypt0r“, utilized a defenselessness in a Windows Server segment to spread inside corporate systems. The shortcoming was first uncovered to the world as a feature of a huge dump of programming vulnerabilities found by the NSA and afterward stolen by a gathering of programmers calling themselves “Shadow Brokers“.
How to Protect Your Networks/PC from Ransomware Attack?
Ransomware is the quickest developing malware risk, focusing on clients of numerous types—from the home client to the corporate system. On normal, more than 4,000 ransomware assaults have happened day by day since January 1, 2016. This is a 300-percent expansion over the around 1,000 assaults for every day seen in 2015. There are exceptionally compelling avoidance and reaction activities that can altogether moderate the hazard postured to your association.
Ransomware targets home clients, organizations, and government arranges and can prompt brief or perpetual loss of touchy or restrictive data, disturbance to customary operations, monetary misfortunes caused to reestablish frameworks and records, and potential damage to an association’s notoriety.
Ransomware may guide a client to tap into a connection to pay an emancipate; be that as it may, the connection might be malignant and could prompt extra malware diseases. Some ransomware variations show threatening messages, for example:
“Your network was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.” “You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
“You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
How You Can Secure Your Networks?
Teach Your Organization
Attackers regularly enter the association by deceiving a client to unveil a secret word or tap on an infection loaded email connection.
Remind workers to never click spontaneous connections or open spontaneous connections in messages. To enhance workforce mindfulness, the inward security group may test the preparation of an association’s workforce with reproduced phishing emails.
Proactive Prevention is the Best Defense
A counteractive action is the best protection against ransomware and it is basic to take precautionary
measures for security. Contaminations can annihilate to an individual or association, and recuperation might be a troublesome procedure requiring the administrations of a legitimate information recuperation
expert. The U.S. Government (USG) suggests that clients and overseers take the accompanying preventive measures to shield their PC systems from succumbing to a ransomware disease:
Take A Look On Some Preventive Measures
• Implement an awareness and training program. Because end users are targets,
employees and individuals should be aware of the threat of ransomware and how it is
delivered.
• Enable strong spam filters to prevent phishing emails from reaching the end users and
authenticate inbound email using technologies like Sender Policy Framework (SPF),
Domain Message Authentication Reporting and Conformance (DMARC), and
DomainKeys Identified Mail (DKIM) to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from
reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
• Patch operating systems, software, and firmware on devices. Consider using a
centralized patch management system.
• Set anti-virus and anti-malware programs to conduct regular scans automatically.
• Manage the use of privileged accounts based on the principle of least privilege: no
users should be assigned administrative access unless absolutely needed, and those
with a need for administrator accounts should only use them when necessary.
• Design get to controls—including document, registry, and system share authorizations— on account of slightest benefit. On the off chance that a client just needs to peruse particular records, the client ought to not have composed access to those records, indexes, or shares.
• Disable full-scale scripts from office records transmitted by means of email. Consider utilizing Office Watcher programming to open Microsoft Office records transmitted by means of the email rather than full office suite applications.
• Implement Software Restriction Policies (SRP) or different controls to forestall programs from executing from basic ransomware areas, for example, transitory organizers supporting prominent Internet programs or pressure/decompression programs, counting the AppaData/LocalAppData organizer.
• Consider handicapping Remote Desktop convention (RDP) in the event that it is not being utilized.
• Use application whitelisting, which just enables frameworks to execute programs known and allowed by security strategy.
• Execute working framework conditions or particular projects in a virtualized condition.
• Categorize information in view of hierarchical esteem and execute physical and intelligent partition of systems and information for various authoritative units.
Few Precautions You Can Use to Continue Your Business
• Backup information routinely. Check the respectability of those reinforcements and test the reclamation procedure to guarantee it is working.
• Conduct a yearly infiltration test and defenselessness evaluation.
• Secure your reinforcements. Guarantee reinforcements are not associated for all time with the PCs, what’s more, systems they are moving down. Illustrations are securing reinforcements in the cloud or physically putting away reinforcements disconnected. A few cases of ransomware have the capacity to bolt cloud-based reinforcements when frameworks persistently move down continuously, additionally known as relentless synchronization. Reinforcements are basic in ransomware recuperation and reaction; on the off chance that you are tainted, a reinforcement might be the most ideal approach to recuperate your basic information.
What to Do If Infected with Ransomware Should preventive measures fail, the USG recommends that organizations consider taking the following steps upon an infection with ransomware:
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking the network or share drives.
• Isolate or power-off affected devices that have not yet been completely corrupted. This may afford more time to clean and recover data, contain damage, and prevent worsening conditions.
• Immediately secure backup data or systems by taking them offline. Ensure backups are free of malware.
• Contact law enforcement immediately. We strongly encourage you to contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately upon discovery to report a ransomware event and request assistance.
• If available, collect and secure partial portions of the ransomed data that might exist.
• If possible, change all online account passwords and network passwords after removing the system from the network. Furthermore, change all system passwords once the malware is removed from the system.
• Delete Registry values and files to stop the program from loading.
How Law Enforcement Can Help?
Any substance tainted with ransomware ought to contact law requirement instantly. Law authorization might have the capacity to utilize lawful specialists and instruments that are inaccessible to most associations. Law authorization can enroll the help of global law requirement accomplices to find the stolen or encoded information or distinguish the culprit. These instruments and connections can incredibly expand the chances of effectively catching the criminal, along these lines forestalling future misfortunes.
Government law requirement puts a need for leading digital examinations in a way that makes minor disturbance a casualty substance’s typical operations and looks to work agreeably what’s more, watchfully with that element. Government law implementation utilizes investigative measures that stay away from superfluous downtime or uprooting of an organization’s representatives. Government law authorization nearly arranges its exercises with the influenced association to evade baseless revelation of data. As an influenced substance recuperates from a
As an influenced substance recuperates from a cyber security occurrence, the element ought to start measures to counteract comparable occurrences. Law implementation offices and the Department of Homeland Security’s National Cybersecurity and Communications Integration Center can help associations in actualizing countermeasures and give data and best practices to keeping away from comparable occurrences later on. Furthermore, the influenced association ought to direct a post-occurrence survey of their reaction to the episode and evaluate the qualities and shortcomings of its occurrence reaction arrange.
Links to Other Types of Malware
Systems infected with ransomware are also often infected with other malware. In the case of CryptoLocker, a user typically was infected by opening a malicious attachment from an email. This malicious attachment contained Update, a downloader, which infected the user with GameOver Zeus. GameOver Zeus was a variant of the Zeus Trojan used to steal banking information and other types of data. After a system became infected with GameOver Zeus, Update would also download CryptoLocker. Finally, CryptoLocker encrypted files on the infected system and demanded a ransom payment. The disruption operation against the GameOver Zeus botnet also affected CryptoLocker, demonstrating the close ties between ransomware and other types of malware. In June 2014, an international law enforcement operation successfully weakened the infrastructure of both GameOverZeus and CryptoLocker.
Please share this article if you find the above information useful… Thanks for spending your time on reading this article. 🙂

32 comments on “How to Protect PC from Ransomware Attack”
special education
May 23, 2017 at 20:11Thank you for the auspicious writeup. It in fact was a amusement account it. Look advanced to far added agreeable from you! However, how can we communicate?
best
May 23, 2017 at 20:11Appreciate this post. Will try it out.
cool health articles
May 24, 2017 at 20:11Hi outstanding blog! Does running a blog such as this require a large amount of work? I’ve virtually no expertise in coding however I had been hoping to start my own blog soon. Anyway, should you have any ideas or techniques for new blog owners please share. I know this is off subject however I just needed to ask. Many thanks!
Brooks
July 15, 2017 at 20:11magnificent issues altogether, you just gained a emblem new reader. What may you recommend about your publish that you made some days ago? Any certain?
borvestinkral
July 18, 2017 at 20:11I am really enjoying the theme/design of your web site. Do you ever run into any browser compatibility problems? A handful of my blog visitors have complained about my website not working correctly in Explorer but looks great in Firefox. Do you have any solutions to help fix this issue?
Brooks
July 30, 2017 at 20:11magnificent issues altogether, you just gained a emblem new reader. What may you recommend about your publish that you made some days ago? Any certain?
find here
August 10, 2017 at 20:11I simply want to say I’m beginner to blogging and site-building and absolutely liked your blog. Most likely I’m going to bookmark your blog post . You definitely come with awesome writings. Thanks a bunch for revealing your webpage.
Mercy Fallaw
August 24, 2017 at 20:11I just like the helpful info you provide in your articles. I’ll bookmark your weblog and take a look at again here regularly. I am relatively certain I’ll be told many new stuff right right here! Best of luck for the following!
Evan Boulette
September 23, 2017 at 20:11I’ve bookmarked your site, and I’m adding your RSS feeds to my Google account.
real
October 4, 2017 at 20:11My spouse and I absolutely love your blog and find nearly all of your post’s to be just what I’m looking for.
Would you offer guest writers to write content for you?
I wouldn’t mind writing a post or elaborating on most of the subjects
you write with regards to here. Again, awesome web log!
Reuben Paquet
November 9, 2017 at 20:11Your writing taste has been amazed me. Thank you, very nice article.
check here
December 17, 2017 at 20:11I just want to tell you that I’m all new to weblog and truly savored this web blog. Very likely I’m planning to bookmark your site . You amazingly have really good stories. Regards for sharing with us your webpage.
Nicole
December 21, 2017 at 20:11Thank you to all the readers for your positive response! 🙂
official site
January 3, 2018 at 20:11I just want to say I am new to blogs and truly loved your web site. Very likely I’m planning to bookmark your blog post . You absolutely come with awesome articles and reviews. Thanks for sharing with us your blog site.
look at this site
January 27, 2018 at 20:11I just want to mention I’m all new to blogging and site-building and truly liked this web-site. Very likely I’m planning to bookmark your blog . You certainly come with awesome articles and reviews. Thanks a bunch for revealing your web-site.
more
February 24, 2018 at 20:11I just want to tell you that I’m new to weblog and actually liked your blog. Almost certainly I’m going to bookmark your blog post . You really come with excellent articles. Cheers for revealing your web-site.
additional hints
March 29, 2018 at 20:11I simply want to mention I am just very new to blogging and definitely loved your web-site. Most likely I’m want to bookmark your blog . You surely have remarkable articles and reviews. Kudos for sharing with us your webpage.
Blogs
April 2, 2018 at 20:11Fantastic!
Leo Tewmey
April 30, 2018 at 20:11I simply wanted to write down a quick word to say thanks to you for those wonderful tips and hints you are showing on this site.
Adelle Animashaun
May 1, 2018 at 20:11I reallyI trulyI seriouslyI absolutely love your blogyour siteyour website.. Very niceExcellentPleasantGreat colors & theme. Did you createdevelopmakebuild this websitethis sitethis web sitethis amazing site yourself? Please reply back as I’m looking totrying toplanning towanting tohoping toattempting to create my ownmy very ownmy own personal blogwebsitesite and would like towant towould love to knowlearnfind out where you got this from or what theexactly what thejust what the theme is calledis named. ThanksMany thanksThank youCheersAppreciate itKudos!
Kendall Chatlos
May 4, 2018 at 20:11No doubt this is an excellent post I got a lot of knowledge after reading good luck. Theme of blog is excellent there is almost everything to read, Brilliant post.
Marco Chladek
May 5, 2018 at 20:11What a fantabulous post this has been. Never seen this kind of useful post. I am grateful to you and expect more number of posts like these. Thank you very much.
Dalene
May 12, 2018 at 20:11I got this web page from my buddy who shared with me regarding this web site and at the moment
this time I am browsing this website and reading very informative
articles or reviews at this time.
Sima
May 13, 2018 at 20:11I always spent my half an hour to read this weblog’s articles all the time
along with a mug of coffee.
Seth
May 21, 2018 at 20:11Thank you for any other informative blog. Where else could
I am getting that kind of information written in such an ideal manner?
I have a mission that I’m simply now operating
on, and I’ve been on the look out for such info.
Jeanette Lathim
May 27, 2018 at 20:11I really can’t believe how great this site is. Keep up the good work. I’m going to tell all my friends about this place.
Swen
June 1, 2018 at 20:11I do not even know how I finished up right here, but I thought this submit was
once good. I do not recognize who you are but definitely you are going to a famous blogger when you are not already.
Cheers!
Addie
June 14, 2018 at 20:11I always spent my half an hour to read this blog’s posts all the time along with
a cup of coffee.
Lettie
July 26, 2018 at 20:11Its like you read my thoughts! You appear to understand
a lot about this, like you wrote the guide in it or something.
I believe that you just could do with some p.c.
to drive the message house a little bit, but other than that, this is fantastic blog.
A fantastic read. I’ll certainly be back.
Jefferey
August 1, 2018 at 20:11Fastidious response in return of this question with
real arguments and describing all regarding that.
Adell
August 3, 2018 at 20:11This is very attention-grabbing, You’re an overly professional blogger.
I have joined your feed and stay up for looking for more of your great post.
Also, I have shared your website in my social networks
Skye
August 15, 2018 at 20:11I’m impressed, I have to admit. Seldom do I encounter a blog that’s equally
educative and interesting, and let me tell you, you’ve hit the nail on the head.
The issue is something that too few people are speaking intelligently
about. I am very happy I found this in my hunt for something regarding this.